Looking for the best proxy for your needs? Discover our comprehensive guide each type of proxy, from basic to advanced options, and find the perfect solution to boost your privacy, security, and online efficiency.
In the increasingly complex world of internet usage, selecting the right proxy for your needs can be challenging. That’s why a thorough guide each type of proxy is essential to help users make the right choice. Whether you are an individual looking for privacy, a company handling massive data, or a digital marketer managing multiple accounts, understanding proxies is key to your online success.
This guide each type of proxy will walk you through from the most basic forms to the advanced options available today. By the end, you’ll be well-equipped to choose the right solution tailored for your purpose.
guide each type of proxy
What Is a Proxy?
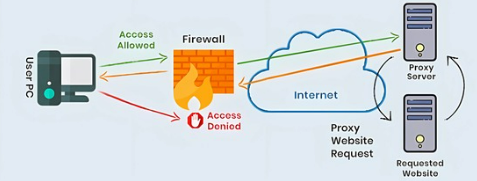
Before diving into the guide each type of proxy, let’s quickly understand what a proxy server is. A proxy acts as a gateway between you and the internet. It hides your real IP address and may modify your requests to better suit your needs — whether that’s faster access, more anonymity, or bypassing geo-blocks.
Using a well-chosen proxy can improve security, allow you to access restricted content, and help you manage multiple online activities without being detected.
Why You Need a Detailed Guide Each Type of Proxy
Choosing the right proxy is more important than most people realize. Without a proper guide each type of proxy, users can easily end up selecting a proxy that doesn’t fit their specific needs, potentially exposing themselves to security risks, slower internet speeds, or unexpected service failures. Every type of proxy comes with its own set of advantages and limitations. Some are built for speed but sacrifice privacy, while others offer strong anonymity but may not support all types of traffic.
By understanding these differences through a detailed guide each type of proxy, you empower yourself to make smarter choices that enhance both your security and efficiency online. Whether you’re aiming to protect sensitive personal information, bypass geo-restrictions, or manage multiple online identities, selecting the correct proxy type is crucial to achieving your goals without compromising your digital safety.
Now, let’s dive deeper into this comprehensive guide each type of proxy and explore how each option works, where it shines, and when it’s best used.

Basic Proxies
In this first level of the guide each type of proxy, we explore the most common and beginner-friendly types:
1. Transparent Proxies
Transparent proxies are often used in public Wi-Fi networks or by companies to monitor users. They don’t offer anonymity because websites can still detect your real IP address.
Use Case: Content filtering, monitoring employee or student activities.
Pros: Easy to set up, no user-side configuration needed.
Cons: No privacy protection.
In our guide each type of proxy, transparent proxies are considered entry-level because they prioritize control over anonymity.
2. HTTP Proxies
HTTP proxies specialize in handling web traffic. If you mostly browse websites, an HTTP proxy is a great start.
Use Case: Accessing blocked websites, caching web content for faster loading.
Pros: Speedy browsing, better content access.
Cons: Limited to HTTP/HTTPS traffic only.
As the guide each type of proxy shows, HTTP proxies are ideal for lightweight users focused on website activities.
Intermediate Proxies
Moving on to intermediate options in our guide each type of proxy, we find more flexible and powerful solutions:
3. SOCKS Proxies
SOCKS proxies, particularly SOCKS5, can handle all types of traffic — not just web pages.
Use Case: Email, P2P downloads, video streaming.
Pros: Versatile and high-performance.
Cons: Slightly slower than HTTP proxies because of less caching.
In the guide each type of proxy, SOCKS proxies are highly recommended for users who need flexibility beyond web browsing.
4. Residential Proxies
Residential proxies route your traffic through real devices and ISP-assigned IP addresses, making it extremely hard to detect.
Use Case: Ad verification, market research, sneaker copping.
Pros: Extremely low detection rate, reliable.
Cons: Expensive compared to other types.
Following the guide each type of proxy, residential proxies are perfect for high-stakes online activities that demand genuine user footprints.
As you can see, selecting the right proxy is not just about picking any option available. It’s about aligning your specific needs with the strengths of each proxy type. Whether you prioritize speed, anonymity, security, or bypassing restrictions, the insights provided in this guide each type of proxy will help you make an informed decision. Always assess factors like reliability, privacy level, cost, and compatibility with your intended activities. Remember, a thoughtful choice today ensures smoother, safer browsing experiences tomorrow. With this guide each type of proxy in hand, you are now better prepared to navigate the digital world confidently and securely.

Advanced Proxies
At the highest level of our guide each type of proxy, we encounter sophisticated tools for professional users:
5. Datacenter Proxies
Unlike residential proxies, datacenter proxies are not associated with an ISP but rather with a corporate data center.
Use Case: Mass data scraping, bulk account creation.
Pros: Fast and cost-effective.
Cons: Easier to detect by websites.
The guide each type of proxy notes datacenter proxies are suited for speed-focused tasks where occasional blocking is acceptable.
6. Mobile Proxies
Mobile proxies use IP addresses assigned by mobile carriers. Since traffic from mobile devices is seen as more legitimate, websites rarely block them.
Use Case: Managing social media accounts, high-trust operations.
Pros: Very high success rate, hard to block.
Cons: Extremely expensive and limited availability.
According to our guide each type of proxy, mobile proxies are the ultimate weapon for professionals needing flawless access and anonymity.
Specialized Proxies
Within the broader landscape of proxies, there are specialized options designed to meet very specific needs. These special cases are essential to understand for users who require more tailored solutions.
Rotating Proxies are a prime example. Instead of sticking with one IP address for an extended period, rotating proxies automatically assign a new IP address either after each request or after a set session duration. This makes them particularly useful for web scraping, data mining, and activities that require a high level of anonymity and avoidance of IP bans. By constantly changing IPs, rotating proxies reduce the risk of detection and help maintain smooth, uninterrupted access.
Another important specialized option is Static Residential Proxies. Unlike rotating proxies, static residential proxies provide a fixed IP address that is associated with a real residential location. This offers the benefit of stability while still retaining the authenticity that residential IPs provide. They are ideal for managing long-term social media accounts, accessing sensitive services, or performing tasks that require a consistent online presence without triggering suspicion.
Then there’s the distinction between Shared vs. Dedicated Proxies. Shared proxies are used by multiple users simultaneously. They are a more affordable choice and can be suitable for less resource-intensive tasks, but users may experience slower speeds and slightly higher risk of being blacklisted due to shared activity. On the other hand, dedicated proxies are assigned to a single user, offering superior speed, better reliability, and enhanced privacy. These are often preferred for serious business operations, sensitive transactions, and personal projects that demand uncompromised performance.
Choosing the right specialized proxy depends heavily on your exact objectives, your tolerance for risk, and the nature of your online activities. Taking the time to understand the differences among these options can make a significant impact on your success in using proxies effectively.
Key Factors to Consider When Choosing
Throughout this guide each type of proxy, remember these critical decision-making factors:
-
Purpose: What task are you aiming to accomplish?
-
Speed: Do you need fast access or is stealth more important?
-
Budget: Are you able to invest in premium solutions like mobile proxies?
-
Security: How critical is anonymity to your activities?
Always match your needs with the right tool as emphasized in the guide each type of proxy.
Final Thoughts
Choosing the right proxy type can seem overwhelming at first. However, with a comprehensive guide each type of proxy, it becomes much easier to navigate through the many options available. Whether you’re a beginner just wanting to access blocked sites or a professional managing thousands of online requests, there is a proxy perfectly tailored for your needs.
Use this guide each type of proxy as a trusted roadmap, and always prioritize trusted providers, strong encryption, and a clear understanding of your objectives. Your perfect browsing experience awaits!

